LinkDaddy Cloud Services Press Release: What You Required to Know
LinkDaddy Cloud Services Press Release: What You Required to Know
Blog Article
Achieve Service Continuity With Secure Cloud Storage Space Provider

Benefits of Secure Cloud Storage Space
Undoubtedly, secure cloud storage space uses organizations a wide range of advantages in terms of information protection and access. By storing data on credible cloud platforms that utilize security and advanced protection steps, services can secure their info from unapproved gain access to or cyber hazards. Overall, the benefits of protected cloud storage space translate into boosted data management, boosted operational performance, and improved safety for services of all sizes.
Trick Features for Business Continuity

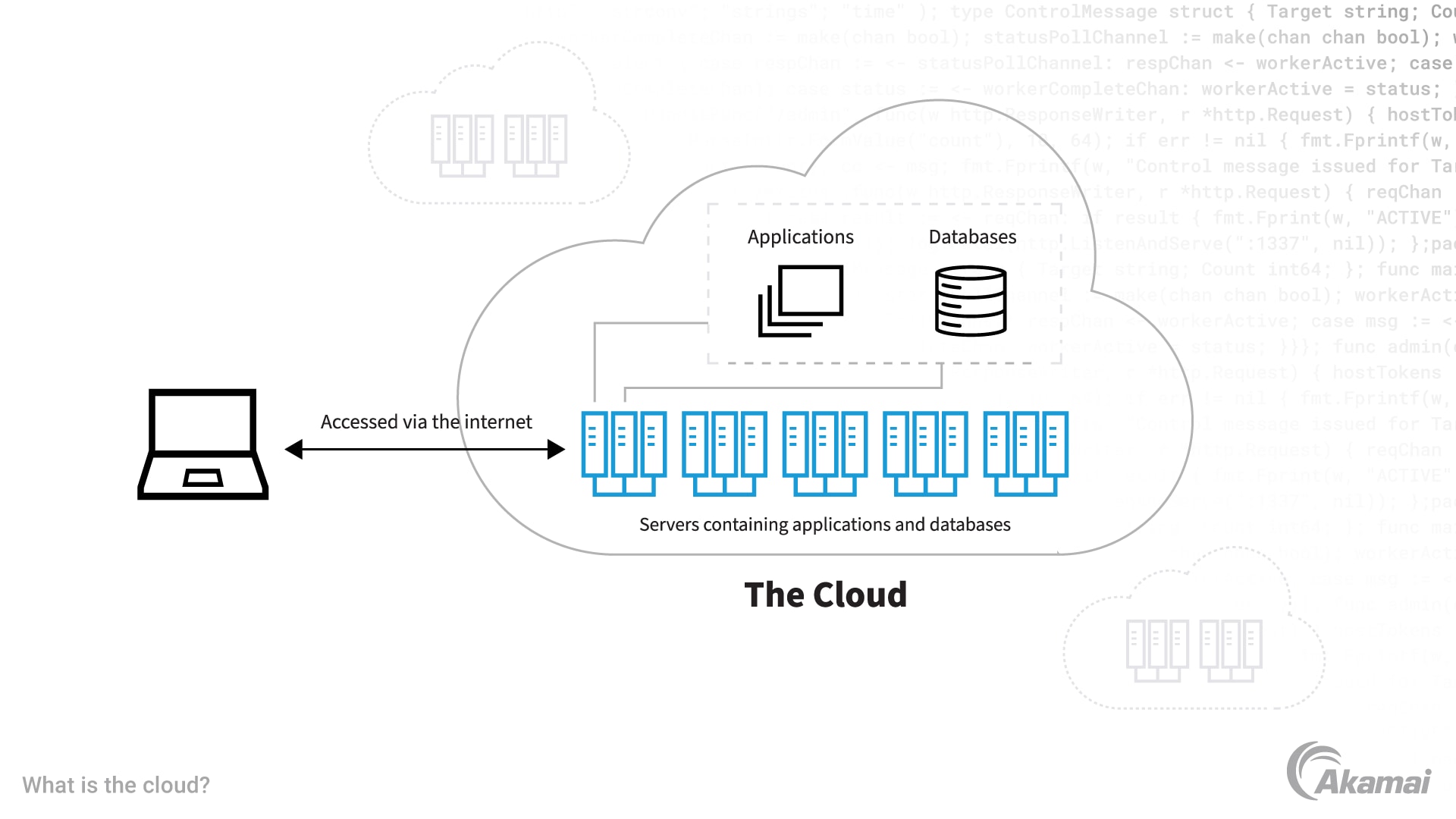
By distributing data across numerous web servers or information facilities, services can minimize the danger of data loss and guarantee constant access to their details. On the whole, these crucial functions function together to form a thorough service connection strategy that safeguards crucial information and operations.
Relevance of Data File Encryption
In today's interconnected electronic landscape, protecting sensitive info is vital, making the significance of data file encryption an essential facet of maintaining data integrity and protection. Information file encryption involves inscribing info in such a method that just authorized parties can access and understand it. By converting data right into a safe and secure style, security works as a shield against unapproved gain access to, reducing the danger of data violations and cyber hazards.
Catastrophe Healing Strategies
A durable calamity healing plan entails detailing procedures to recover information, applications, and IT facilities in the event of a catastrophe. One essential facet of a reliable technique is normal information back-ups. By More Help storing information in secure cloud storage space solutions, businesses can guarantee that crucial information is protected and quickly accessible in case of a disaster.
Picking the Right Provider
To make sure seamless company continuity and effective calamity recuperation, picking a reputable and ideal provider for safe cloud storage space is critical. When choosing a cloud storage space service provider, several key factors should be considered. Review the copyright's security procedures. Ensure they utilize robust security approaches, have rigid accessibility controls, and adhere to sector regulations to secure your data. Furthermore, evaluate the provider's data healing capacities. A reputable provider ought to offer routine backups, redundancy measures, and effective healing procedures to minimize downtime in situation of a calamity.
Your business requirements may develop over time, so it's essential to select a supplier that can fit your expanding storage space needs and adapt to transforming scenarios. By meticulously examining these variables, you can pick a cloud storage service supplier that aligns with your service's requirements and makes sure continuous procedures in the face of prospective interruptions.
Final Thought
In final thought, this page secure cloud storage services provide vital advantages for achieving business continuity, including enhanced safety and security features, seamless scalability, efficient cooperation tools, durable data backup mechanisms, and calamity healing techniques. Data security plays a vital role in safeguarding sensitive info, while selecting the appropriate service copyright is crucial to making certain conformity with policies and preserving operational effectiveness. try here linkdaddy cloud services press release. Safe cloud storage space is a beneficial property in today's digital landscape for making certain uninterrupted business operations
Data backup mechanisms are important for protecting versus data loss due to system failures, cyber-attacks, or human mistakes. By dispersing data across numerous servers or data facilities, companies can mitigate the danger of data loss and make sure continuous accessibility to their details.In today's interconnected digital landscape, guarding sensitive details is extremely important, making the significance of data file encryption a basic aspect of keeping data integrity and safety and security. By converting data right into a safe layout, encryption acts as a shield against unapproved gain access to, minimizing the risk of data violations and cyber hazards.
Conformity demands and data defense laws commonly mandate the use of encryption to guard delicate information, highlighting its important duty in modern information safety and security strategies.
Report this page